Content Security error from browser
Table of Contents

Content Security Error Message
If you’re operating a third-party service on the website, you may receive an error inside the browser that says Content Security Policy of your site blocks some resources.
It is an easy fix and can be achieved with a few clicks:
Solution
Below, is the solution to investigate and apply to show iFrames on a site:
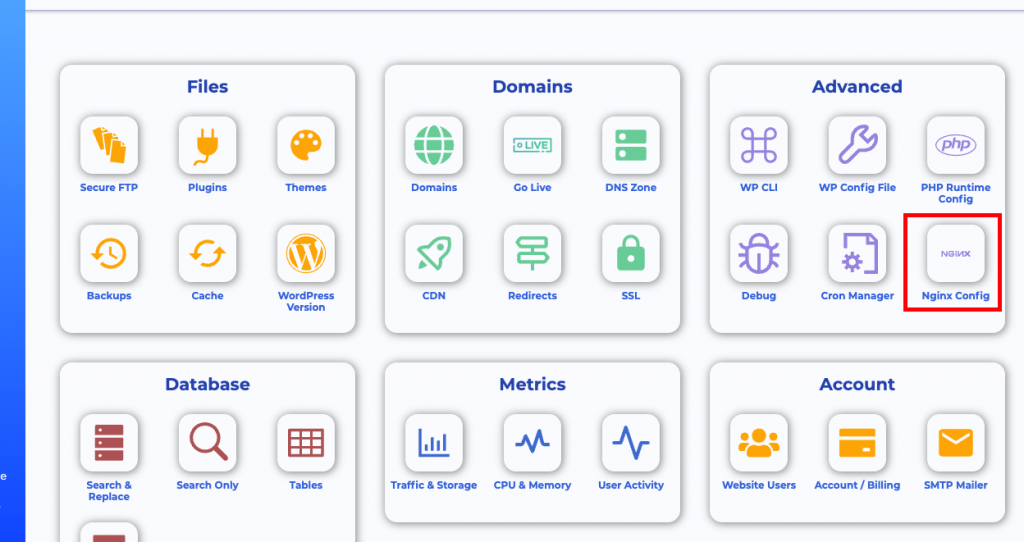
Step 1
Go to the Staq Panel of the website in question and click Nginx Config:
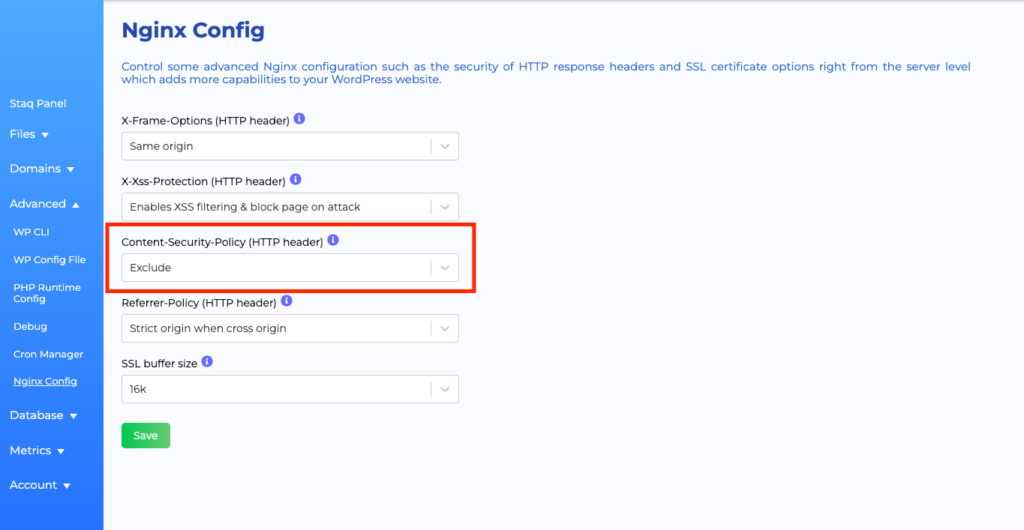
Step 2
Then, under Content-Security-Policy (HTTP header), click Exclude, then Save:
Refresh local browser
Then, refresh your local browser to see if this rectifies the problem.
You may need to clear your cookies as well.
Try Staq
Everything WordPress in one place. Simplify WordPress, streamline your flow